[#29890] - [4.0] Password min length validation on login page
- Closed
- 3 Jul 2020
- Medium
- Build: staging
- # 29890
Steps to reproduce the issue
Joomla 4.0-dev - install as standard with no sample data
For example. My test case credentials are u: admin p: admin (5 chars, meets current 4 char minimums)
Login as an admin in /administrator/
Manage Users -> Options -> Set Password Min Length to something higher, lets say 10 -> Save - the Joomla minimum password length is now 10 chars.
visit http://example.com/index.php?option=com_users&view=login
You will now see a login page, and a login module.
View the source of the password field in the PAGE (not the right module, we will come to that in a moment)
[Linebreaks mine to make it clearer in GitHub]
<input type="password" name="password" id="password"
value="" autocomplete="current-password"
class="form-control validate-password required" size="25" maxlength="99"
required="" data-min-length="10"
>note the data-min-length="10" attribute!
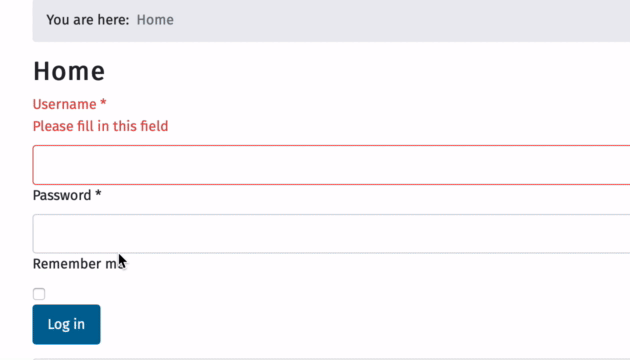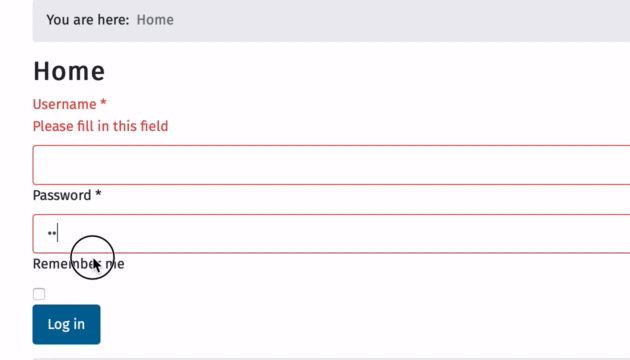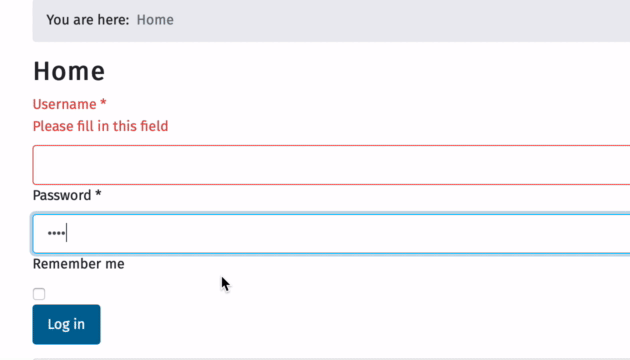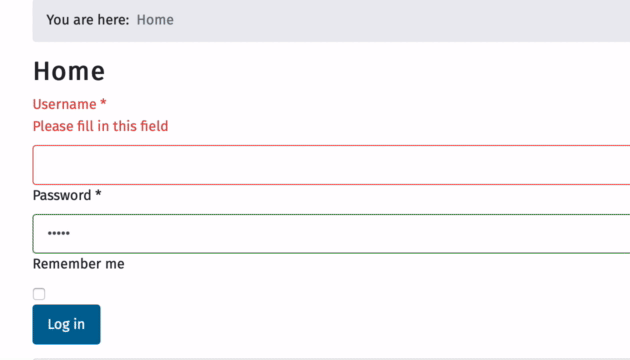
Ok now watch, Im entering one char at a time and then blur by clicking out of the password box
Note that it only takes FOUR chars before it accepts the input, instead of the expected 10 chars set in admin and set by the data-min-length
Next lets look at the password field in the MODULE on the right, note the html is
<input id="modlgn-passwd-16" type="password" name="password" autocomplete="current-password" class="form-control" placeholder="Password">Note there is NO data-min-length="10" attribute!
Note that this password field (in the module) DOESNT need 4 chars as there is no annoying javascript validation on it at all.
Just a quick check -
- the login page at /administrator/ doesnt have the
data-min-length="10"attribute either - the login page at /administrator/ doesnt have the annoying 4 char minimum input for validation either
Expected result
-
Both password fields should have the
data-min-length="10"attribute - or neither should - if its there then I assume its for the passwordstrength JS which doesnt appear to even be running on this page. -
if the min length configured is 10 then the field should not be accepting just 4 to validate
-
Is showing the minimum char of a password a security issue? it gives away an important figure to brute forcers? I dont know, lets tag @joomla/security @SniperSister and the JSST can decide.
Personally, and my opinion is not important, I think the correct course of action is to remove ALL Javascript validation from the password field (and username field!), and to remove the data-min-length attribute from all frontend password fields.
Actual result
Described in narrative above.
System information (as much as possible)
Safari on Mac.
Additional comments
No console errors.
The rule on password length can only be applied to new passwords otherwise existing users cannot log in
Is showing the minimum char of a password a security issue?
IMO no, because a well designed UI will explain the password complexity rules on the registration page or any edit form where you can update a password (which includes length and required character combinations). You might have a stronger argument if there is no frontend registration, but if you think this data attribute is an information leak then any error message which provides guidelines on password requirements is as well.
I personally agree with Michael on the point of that this not be an security issue by itself. It might even tells them only that they don't have to try brute forcing given that 12 oder 10 is just the minimum but we all know they dont care and still throw wp-login against sites that can clearly be identified as joomla sites :D
Cool - I agree its not a security issue then, especially if the password complexity rules are being published for registration, I forgot about that.
That being the case though, still has no affect on the actual reported issue here.
| Status | New | ⇒ | Closed |
| Closed_Date | 0000-00-00 00:00:00 | ⇒ | 2020-07-03 06:05:45 |
| Closed_By | ⇒ | SharkyKZ |
I agree. I wasn't aware that this stupid validation exists here.
Would be an absolute no-go to validate the pw using the min-length value.
If a super user changes the password settings then it must be possible for users to login with the old password even if it's shorter. E.g. if super users want to force the new settings then they can activate "Require Password Reset" but users can't log in with their old, shorter pw.