[#34185] - [4][Security - Release Blocker] Mail Templates can be used to access files outside of webspace.
- Closed
- 26 May 2021
- Medium
- Build: staging
- # 34185
Steps to reproduce the issue
On simple code review... /facepalm
Assume my JPATH_BASE = /application
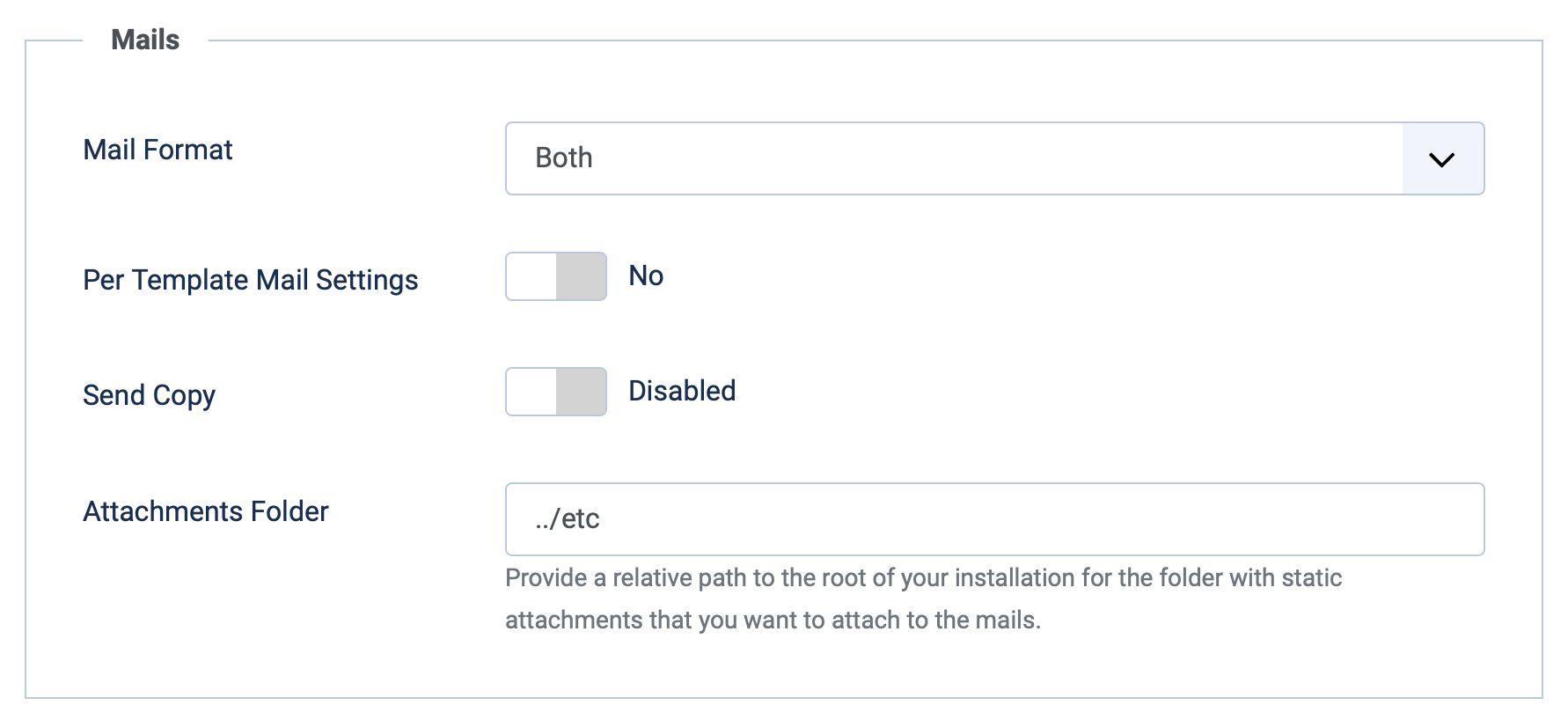
System -> Mail Templates -> Options
Set Attachments Folder to a relative path from your webspace to the /etc folder (as an example). On my docker thats ../etc as my JPATH_BASE is /application
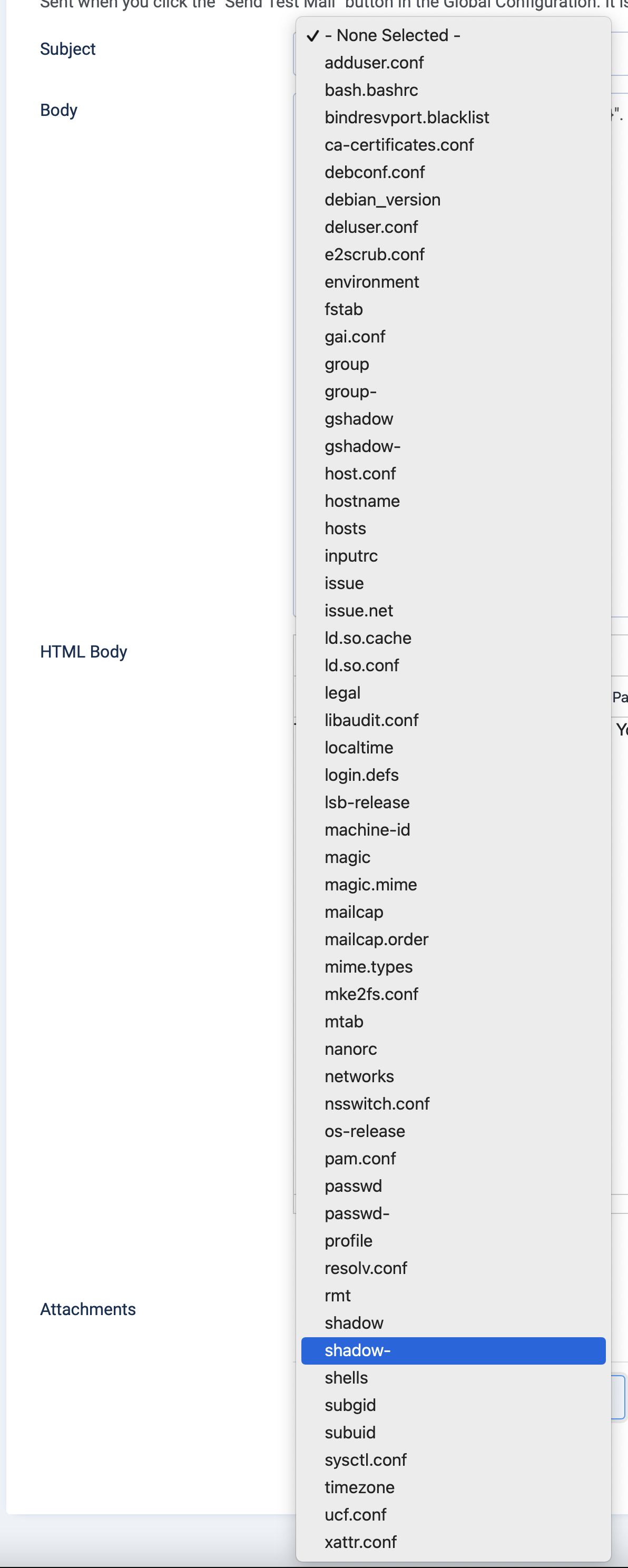
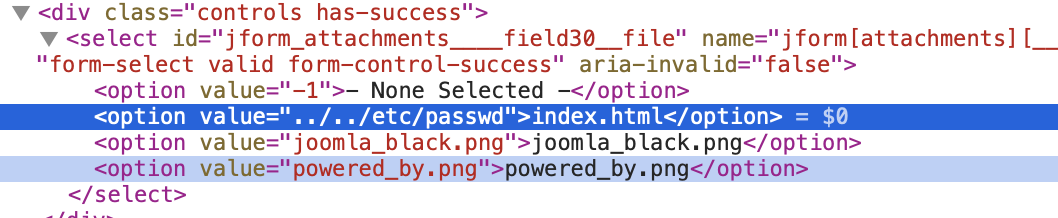
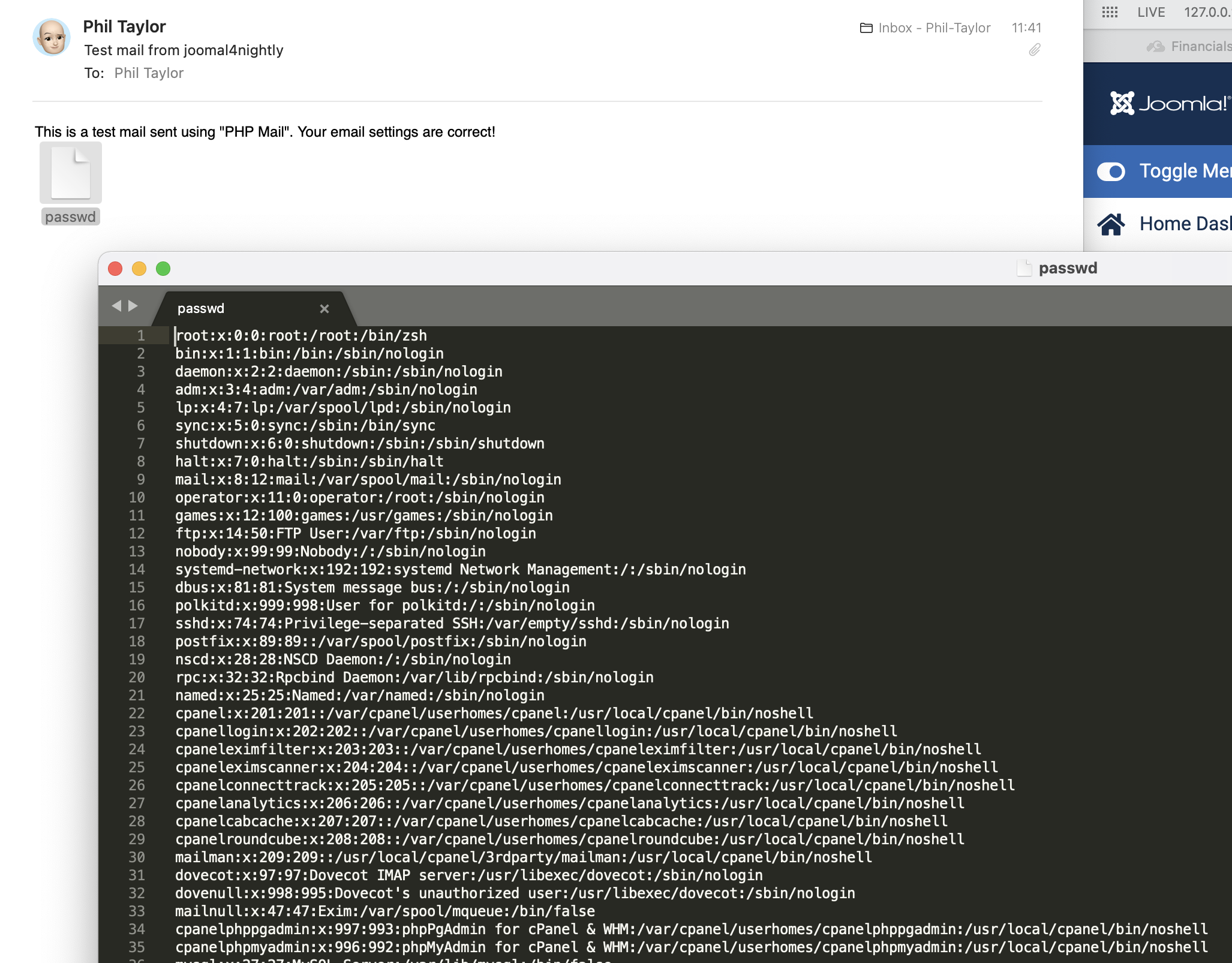
System -> Mail Templates -> "Global Configuration: Test Mail - en-GB" (as an example) select the file in the dropdown, note you can see all the files in /etc - I selected passwd and called it hacked.
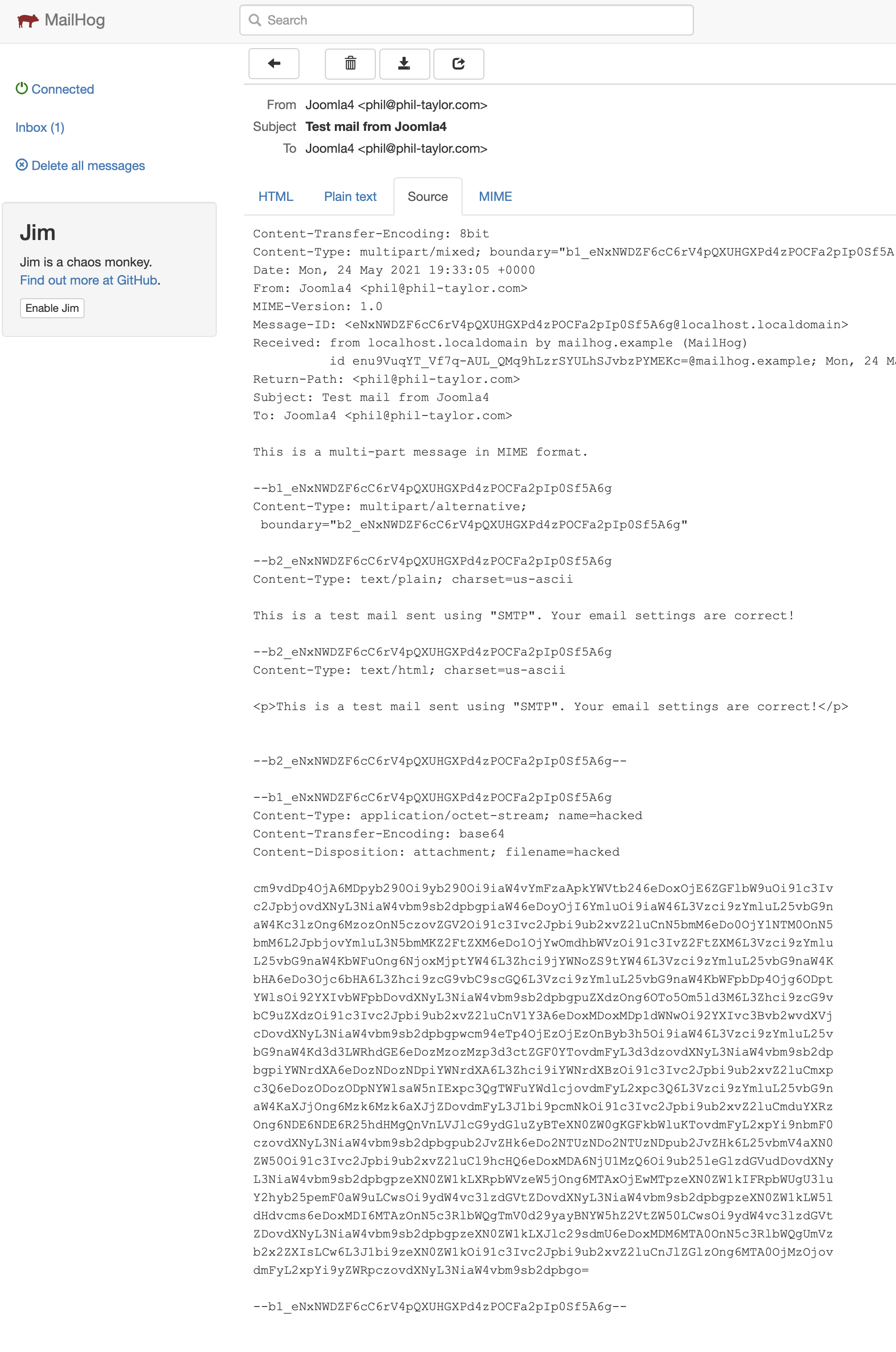
Save the options and then use Global Config to send this test email (which uses the mail templates configuration)
Inspect the email - see that the passwd file has indeed been attached to the email..
Expected result
Mail Templates, and Attachments, should be restricted to JPATH_BASE and below.
The relative path should not accept .. as a part of the path etc..
You know, security 101... /facepalm
Things to fix:
- Validation and filtering and locking to JPATH_BASE of relative path when entering in options
- Checking and cleaning and locking to JPATH_BASE of this path before using it to attach files to emails
Actual result
Ability to see restricted system files in select box
Ability to email files from outside JPATH_BASE as attachments - full files emailed.
Additional comments
Yes I know it depends on your server configuration and permissions for folders/files etc... my set up is a docker container with PHP running as fpm, and it can still explore the other folders on the container... so it is a genuine issue.
| Labels |
Added:
?
|
||
I actually thought this to be intended behavior when writing this, since I'd like to have these files outside of the web root, but you are right, this is wrong and we need to fix this.
hm, I suspect on your local test environment "Open basedir" is empty,
or does PHP "Open basedir" path allow it? should not be
Joomla is mass market software. It should not have to rely on a certain PHP configuration
The majority of professional webhosts don't have open basedir set! They might use some other kind of account isolation also.
This is not a hosting issue. This is a Joomla security bug.
Yeah, but you did not answered.
Nevermind.
@Fedik you are correct about open basedir but @PhilETaylor is correct as well - joomla has to address this
- Because I'm in bed unwell from COVID vaccination side effects for the next 12 hours and docker doesn't run on iPhones as far as I know
- Because the setting of open basedir is totally irrelevant to this bug. I would expect if it was set the PHP would stay within those paths, that's the whole point of that PHP config and it's not the Joomla project's responsibility to fix PHP features.
- Regardless of the PHP open basedir setting, Joomla should not be providing a gui tool to explore outside the site
If the media manager or template manager allowed this - there would have been uproar about it! Therefore Same applies here in mail templates.
As a test, I just used a "free account" on "Joomla's OFFICIAL hosting/trial provider" https://launch.joomla.org, and I was able to send myself confidential information from their servers.
I then repeated the test on cPanel, "For over 20 years [...]the leading hosting automation platform".. and I was also able to get the passwd file from the /etc folder emailed to me.
In order to exploit this, all a hacker has to do is a simple SQL injection to the database (as all the settings needed are stored in the db) so to the critics that will say you can only exploit this by logging into admin and setting bad values are wrong. An attacker could use a SQL injection hole in a 3pd extension from the frontend, and then they could configure Mail Templates to attach EVERY FILE from /etc to EVERY EMAIL ever sent from the site... they could then just register, and then the welcome email on the registration would have the files attached...
Mail Templates allows unlimited files to be attached to the emails.
Its not even about /etc. The above exploit could be used to download your Akeeba Backups, your configuration.php file, or literally any file in your webspace. (yes yes yes I know that the SQL Injection vulnerability has to exist first, but seriously, there have been 100s of those in 3pd...)
I would say this proves conclusively that this issue is an issue - regardless of the conversation about open_basedir.
| Labels |
Added:
?
|
||
It seems we need to validate if the folder and file is inside JPATH_ROOT somehow,
because we do not have any kind of API for "private folder".
Or maybe any better idea?
It seems we need to validate if the folder and file is inside JPATH_ROOT somehow,
Like we do everywhere else in Joomla - yes.
because we do not have any kind of API for "private folder".
Correct.
Or maybe any better idea?
Well I understand the point already made that the attachments might want to be private files that are not in the webspace, so maybe for this feature we could accept one folder above JPATH_BASE, but that would be a departure from all previous security restrictions in Joomla, and would still allow this issue if a site was in a first level folder like /application (which ironically my docker containers are), but after several recent conversations with Nic from Akeeba, we also discovered several German web hosting companies that have virtual filesystems where Joomla sees itself in a folder only one above the root.
That could do the trick: https://github.com/joomla/joomla-cms/blob/staging/administrator/components/com_media/config.xml#L51-L52
Ive yet to throw considerable mud at that to see what sticks, but from the shortest code review I can see that this is not strictly enforced either /facepalm but I will not talk about that here as that relates to Joomla 3, and the JSST have responsibility for that. Remember that using Joomla Admin Console is only one way to manipulate the database... nuff said.
| Status | New | ⇒ | Closed |
| Closed_Date | 0000-00-00 00:00:00 | ⇒ | 2021-05-26 16:25:34 |
| Closed_By | ⇒ | richard67 | |
| Labels |
Added:
?
Removed: ? |
||
| Labels |
Removed:
?
|
||
Confirmed