[#30886] - [4] Joomla can send HSTS header over HTTP
- Closed
- 3 Oct 2020
- Medium
- Build: staging
- # 30886
Steps to reproduce the issue
Edit System - HTTP Headers plugin in Joomla 4
Enable Strict-Transport-Security (HSTS)
Visit the site over http:// (NOT https)
Inspect headers
Expected result
Joomla should never send a Strict-Transport-Security (STS) header when accessed over http:// urls
https://tools.ietf.org/html/rfc6797 states VERY CLEARLY in 7.2 that
An HSTS Host MUST NOT include the STS header field in HTTP responses conveyed over non-secure transport.
https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Strict-Transport-Security states lightly restrictive
The Strict-Transport-Security header is ignored by the browser when your site is accessed using HTTP
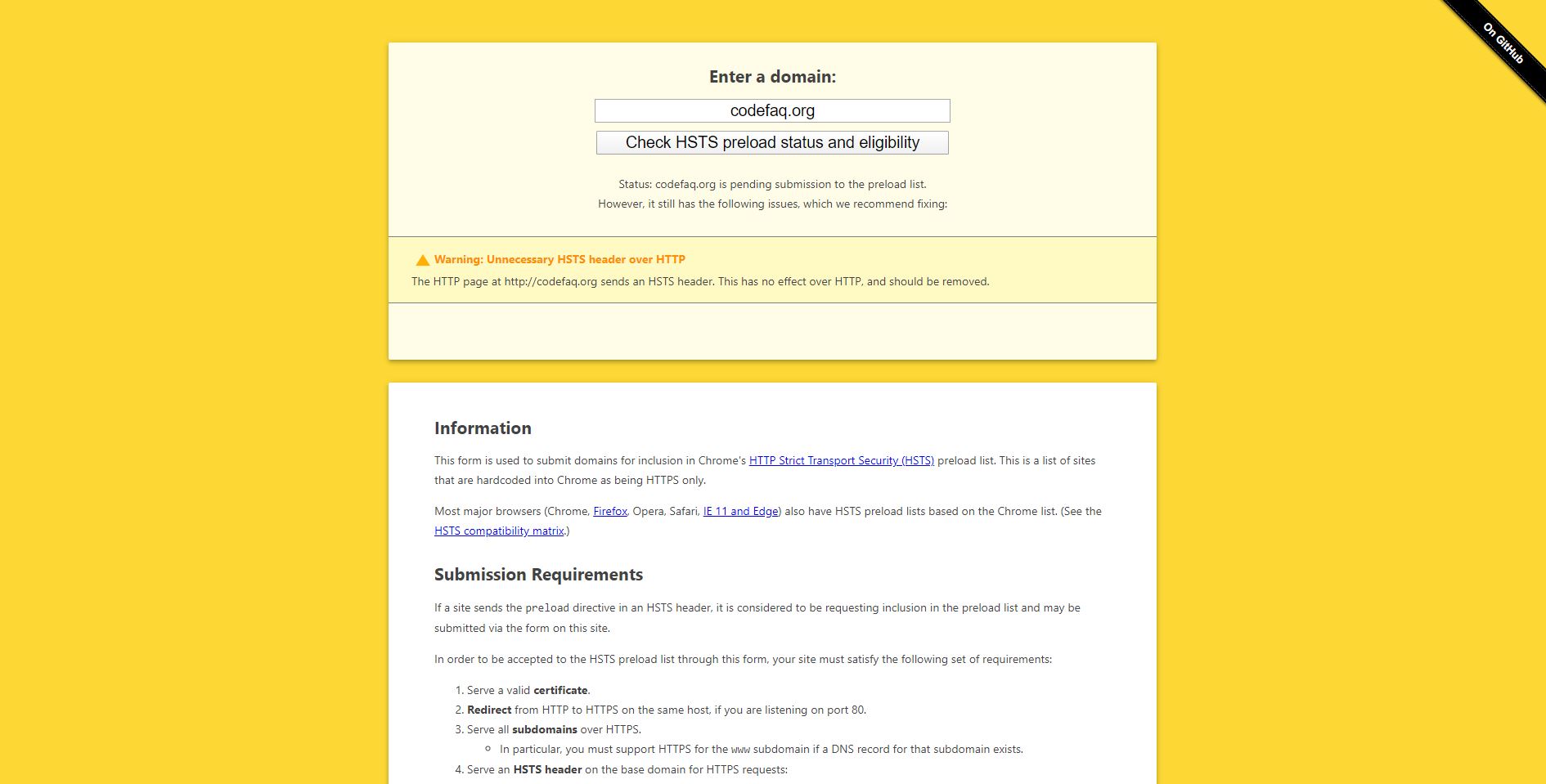
And one of the reasons for getting this right, is the https://hstspreload.org submission process will give a WARNING if it sees the STS header when accessed over http (generic google found image below):
Status: yourdomain.com is pending submission to the preload list.
However, it still has the following issues, which we recommend fixing:
Warning: Unnecessary HSTS header over HTTP
The HTTP page at http://yourdomain.com sends an HSTS header. This has no effect over HTTP, and should be removed.
Actual result
A header like this, is still sent even though the site was accessed over HTTP and not HTTPS.
Strict-Transport-Security: max-age=31536000; includeSubDomains
| Labels |
Added:
?
|
||
| Title |
|
||||||
the browser should not allow you to access that site via http once you have set hsts right?
Incorrect.
If your domain is in the Google Preload List then correct. But the header itself is ignored by browsers (according to Mozilla) when accessed over http://
The first time your site is accessed using HTTPS and it returns the Strict-Transport-Security header, the browser records this information, so that future attempts to load the site using HTTP will automatically use HTTPS instead.
When the expiration time specified by the Strict-Transport-Security header elapses, the next attempt to load the site via HTTP will proceed as normal instead of automatically using HTTPS.
Whenever the Strict-Transport-Security header is delivered to the browser, it will update the expiration time for that site, so sites can refresh this information and prevent the timeout from expiring. Should it be necessary to disable Strict Transport Security, setting the max-age to 0 (over a https connection) will immediately expire the Strict-Transport-Security header, allowing access via http.
The header should not be sent over http, only https.
Maybe there is an exception for localhost?
There is not. The big yellow screenshot is from https://hstspreload.org/ which is the site you go to get your domain listed into the Google Chrome Preload List.
Ok thanks will take a look into that.
| Status | New | ⇒ | Closed |
| Closed_Date | 0000-00-00 00:00:00 | ⇒ | 2020-10-03 08:34:20 |
| Closed_By | ⇒ | zero-24 |
PR: #30902 please test @PhilETaylor
Hmm the browser should not allow you to access that site via http once you have set hsts right? Thats the point of the header to tell the browser to always use https. Or i'm missing something? Maybe there is an exception for localhost?